Caution: The majority of spam nowadays is believed to be sent from hijacked or zombie workstations running a rudimentary SMTP server implementation, with the hosts operator unaware. These zombie machines rarely, if ever, seek to retry failed delivery attempts, as a normal SMTP server would. As a result, if the distribution attempt is blocked by the SonicWall RBL filter, no more attempts to send the spam will be made.
Resolution for SonicOS 6.5
This update offers significant user interface changes as well as a slew of new functionality not found in SonicOS 6.2 or prior firmware. Customers running SonicOS 6.5 firmware should use the following resolution.
Configuring Real Time Blacklist (RBL) Filter
- Access the SonicWall Management Interface by logging in.
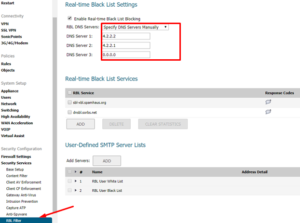
- RBL Filter may be found under Manage | Security Services | RBL Filter.
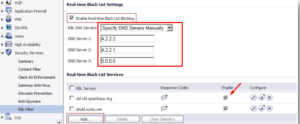
- Activate the checkbox Activate the Real-Time Black List Blocking feature.
- You can set DNS servers under the RBL DNS Servers menu. Inherit Settings from WAN Zone or Manually Specify DNS Servers are two options. If you choose Manually Specify DNS Servers, fill in the DNS Server boxes with the DNS server addresses.
When you enable Real-time Black List Blocking, each enabled RBL service is checked against each enabled RBL service with a DNS request to the DNS servers set under RBL DNS Servers in enabled inbound connections from hosts on the WAN or outbound connections to hosts on the WAN.
NOTE: The RBL Services sbl-xbl.spamhaus.org and dnsbl.sorbs.net are pre-configured by default, and SonicWall will query them to determine the source of spam.
TIP: Statistics are kept in the RBL Service table for each RBL Service and may be accessed by hovering your cursor over the (statistics) icon to the right of the service item.
Add additional RBL Services
By clicking the Add button, you may add more RBL services to the Real-time Black List Services area.
You specify the RBL domain to be queried, enable it for use, and describe the expected answer codes in the Add RBL Domain window. The responses provided by most RBL providers are listed on their websites, though selecting Block All Responses is often acceptable.
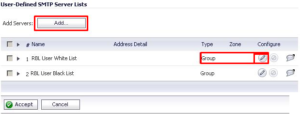
User-Defined SMTP Server Lists
Address Objects can be used to create a white-list (explicit allow) or black-list (explicit deny) of SMTP servers in the User Defined SMTP Server Lists section. The RBL querying procedure will be bypassed for entries in this list.
To make sure you always receive SMTP connections from a partner site’s SMTP server, for example:
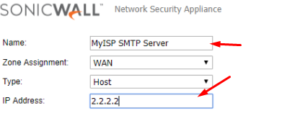
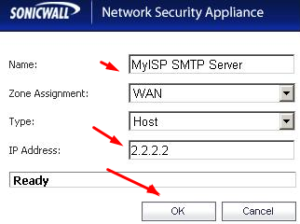
– For the server you added with the Add button, create an Address Object.
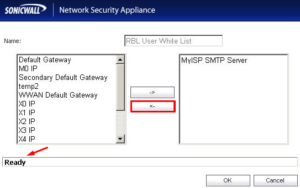
Add the Address Object by clicking the edit icon in the Configure column of the RBL User White List row. The table will be changed, and that server will be allowed to send and receive SMTP messages at all times.
The Monitor | Dashboard page also has a Real-time Black List Lookup function that may be used to test certain SMTP IP addresses (or RBL services, or DNS servers).
Refer here for a list of known spam sources to test with http://www.spamhaus.org/sbl/latest.lasso
Resolution for SonicOS 6.2 and Below
Customers running SonicOS 6.2 and earlier firmware should use the following resolution. We recommend upgrading to the latest general version of SonicOS 6.5 firmware for firewalls that are generation 6 and newer.
Configuring Real-Time Blacklist (RBL) Filter
- Access the SonicWall Management Interface by logging in.
- Go to RBL Filter | Anti-Spam.
- Activate the checkbox Activate the Real-Time Black List Blocking feature.
- You can set DNS servers under the RBL DNS Servers menu. Inherit Settings from WAN Zone or Manually Specify DNS Servers are two options. If you choose Manually Specify DNS Servers, fill in the DNS Server boxes with the DNS server addresses.
When you enable Real-time Black List Blocking, each enabled RBL service is checked against each enabled RBL service with a DNS request to the DNS servers set under RBL DNS Servers in enabled inbound connections from hosts on the WAN or outbound connections to hosts on the WAN.
NOTE: The RBL Services sbl-xbl.spamhaus.org and dnsbl.sorbs.net are pre-configured by default, and SonicWall will query them to determine the source of spam.
TIP: Statistics are kept in the RBL Service table for each RBL Service and may be accessed by hovering your cursor over the (statistics) icon to the right of the service item.
Add additional RBL Services
By clicking the Add button, you may add more RBL services to the Real-time Black List Services area.
You specify the RBL domain to be queried, enable it for use, and describe the expected answer codes in the Add RBL Domain window. The responses provided by most RBL providers are listed on their websites, though selecting Block All Responses is often acceptable.
User-Defined SMTP Server Lists
Address Objects can be used to create a white-list (explicit allow) or black-list (explicit deny) of SMTP servers in the User Defined SMTP Server Lists section. The RBL querying procedure will be bypassed for entries in this list.
For example, to ensure that SMTP connections from a partner site’s SMTP server are always received.
– For the server you added with the Add button, create an Address Object.
– Add the Address Object by clicking the edit icon in the Configure column of the RBL User White List row. The table will be changed, and that server will be allowed to send and receive SMTP messages at all times.
A Real-time Black List Lookup tool is also available on the System | Diagnostics page, which allows SMTP IP addresses (or RBL services, or DNS servers) to be individually examined.
Refer here for a list of known spam sources to test with http://www.spamhaus.org/sbl/latest.lasso